In-Memory Runtime Encryption
1. Overview
When sensitive data such as API keys, access tokens, or private credentials are used by the application, they temporarily reside in heap memory. To reduce the chance of malware or memory scanners locating these secrets, we leverage a specialized in-memory protection layer built with memguard. This ensures sensitive information is stored in locked, guarded, and short-lived memory regions, preventing accidental exposure or persistence after use.
While in-memory runtime encryption significantly reduces the risk of side channel attacks, it does not fully eliminate them 100% and is not a full replacement for a fully TEE (Trusted Execution Environment) environment similar to Confidential VM.
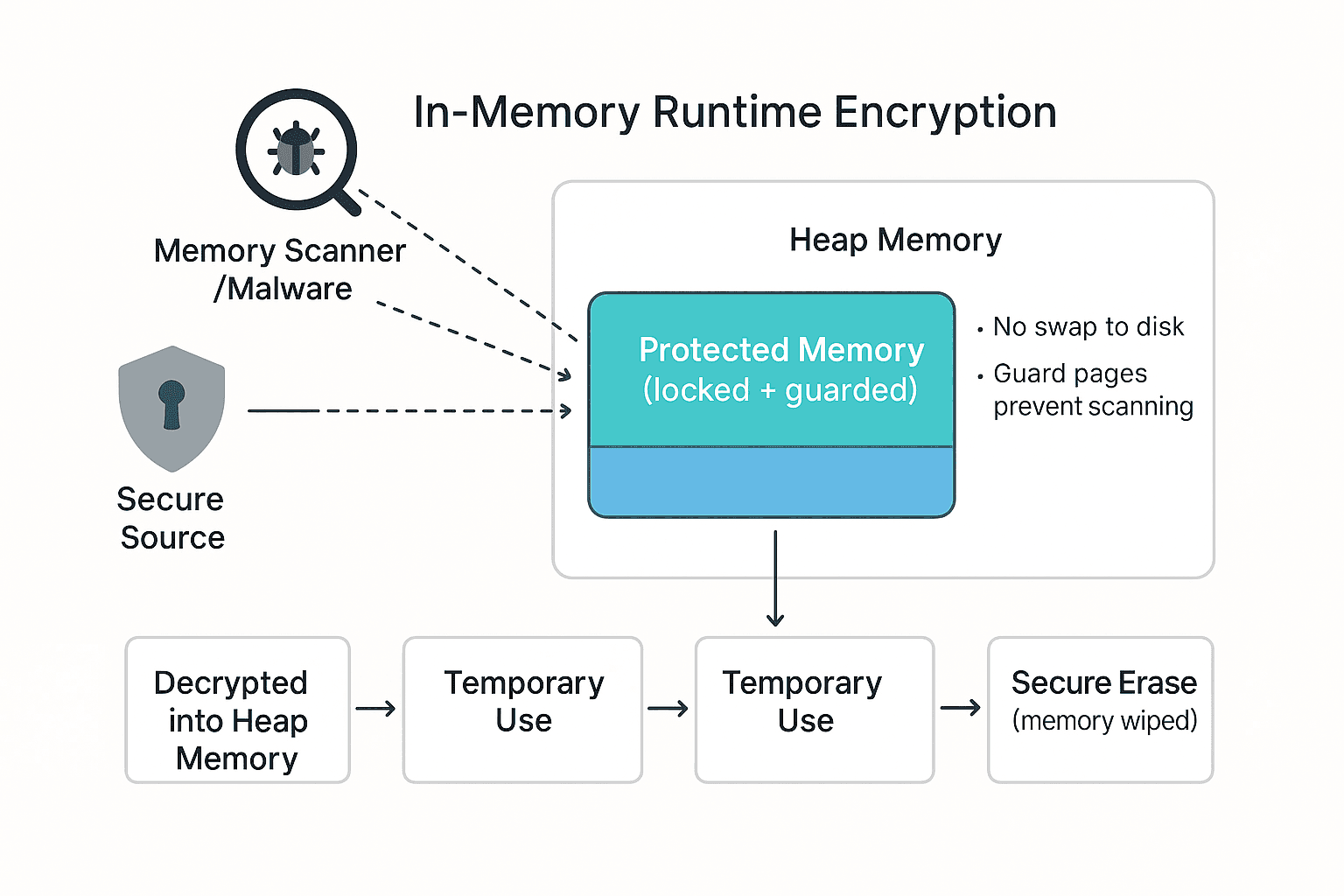
In-Memory Runtime Encryption: Protect Sensitive Keys and Credentials from Memory Scanners and Malware with Locked, Guarded Heap Memory.
2. Why It Matters
Even with encryption at rest and in transit, secrets can still be exposed while in use — when decrypted for runtime operations. Memory attacks often target this exact window by scanning the process heap for recognizable key patterns.
By isolating credentials in guarded memory:
- Data is locked to physical RAM, not swapped to disk.
- Memory pages are surrounded by guard regions that detect or block access attempts.
- Buffers are explicitly wiped after use.
- The secret's lifetime in memory is minimized to milliseconds or seconds.
This approach provides defense-in-depth against runtime credential harvesting and in-process malware.
3. Architecture Overview
3.1 Decryption and Loading
Sensitive data (e.g., API keys or tokens) are decrypted from secure storage or retrieved from a secret manager, then placed directly into protected heap memory.
3.2 Guarded Memory Zone
Once loaded, the data is kept in a memguard-protected enclave:
- Non-swappable (mlock-based protection)
- Surrounded by guard pages
- Automatically destroyed on error or end of scope
3.3 Ephemeral Access
The protected data is only accessed briefly during operations that require it (e.g., authentication, signing, or encryption). No permanent copies are created elsewhere in memory.
3.4 Immediate Zeroing
After the operation, the memory buffer is securely wiped and released, leaving no recoverable traces of the secret.
4. Summary
Sensitive credentials are decrypted only into guarded heap memory, isolated from standard process space. They are used briefly, wiped immediately, and never written to logs or disk — ensuring that even a compromised host or memory inspection attempt cannot recover secrets in use.