Container Security and Build Provenance
This document outlines how Fystack ensures verifiable, tamper-resistant container builds through SLSA-compliant provenance, keyless cryptographic signing, and public transparency logs. It allows us to prove that every production container image originates from a specific Git commit and has not been tampered with.
1. Overview
Each production image is built using Docker BuildKit with embedded SLSA Level 3 provenance and SPDX SBOM metadata. All artifacts are keylessly signed using Sigstore Cosign and recorded in the Rekor transparency log, creating an immutable audit trail.
Integrity Chain:
Integrity Chain
Git Commit → SLSA Provenance → Cosign Signature → Rekor Transparency Log
Distroless Base Images
Fystack uses distroless images to minimize attack vectors from the operating system. Distroless images contain only the application and its runtime dependencies, eliminating package managers, shells, and other utilities that could be exploited.

Distroless Dockerfile
FROM golang:1.25 AS builder
ARG TARGETOS=linux
ARG TARGETARCH=amd64
WORKDIR /src
COPY go.mod go.sum ./
RUN --mount=type=cache,target=/go/pkg/mod \
go mod download
COPY . .
RUN --mount=type=cache,target=/go/pkg/mod \
--mount=type=cache,target=/root/.cache/go-build \
CGO_ENABLED=0 GOOS=${TARGETOS} GOARCH=${TARGETARCH} \
go build -o /out/mpcium ./cmd/mpcium
FROM gcr.io/distroless/base-debian12:latest
USER nonroot:nonroot
WORKDIR /app
COPY --from=builder /out/mpcium /app/mpcium
ENTRYPOINT ["/app/mpcium"]
This approach:
- Reduces the attack surface by eliminating unnecessary OS packages
- Runs as a non-root user for additional security
- Uses BuildKit cache mounts for faster, more efficient builds
- Produces minimal final images (typically <20MB for Go binaries)
2. Build Provenance & Signing
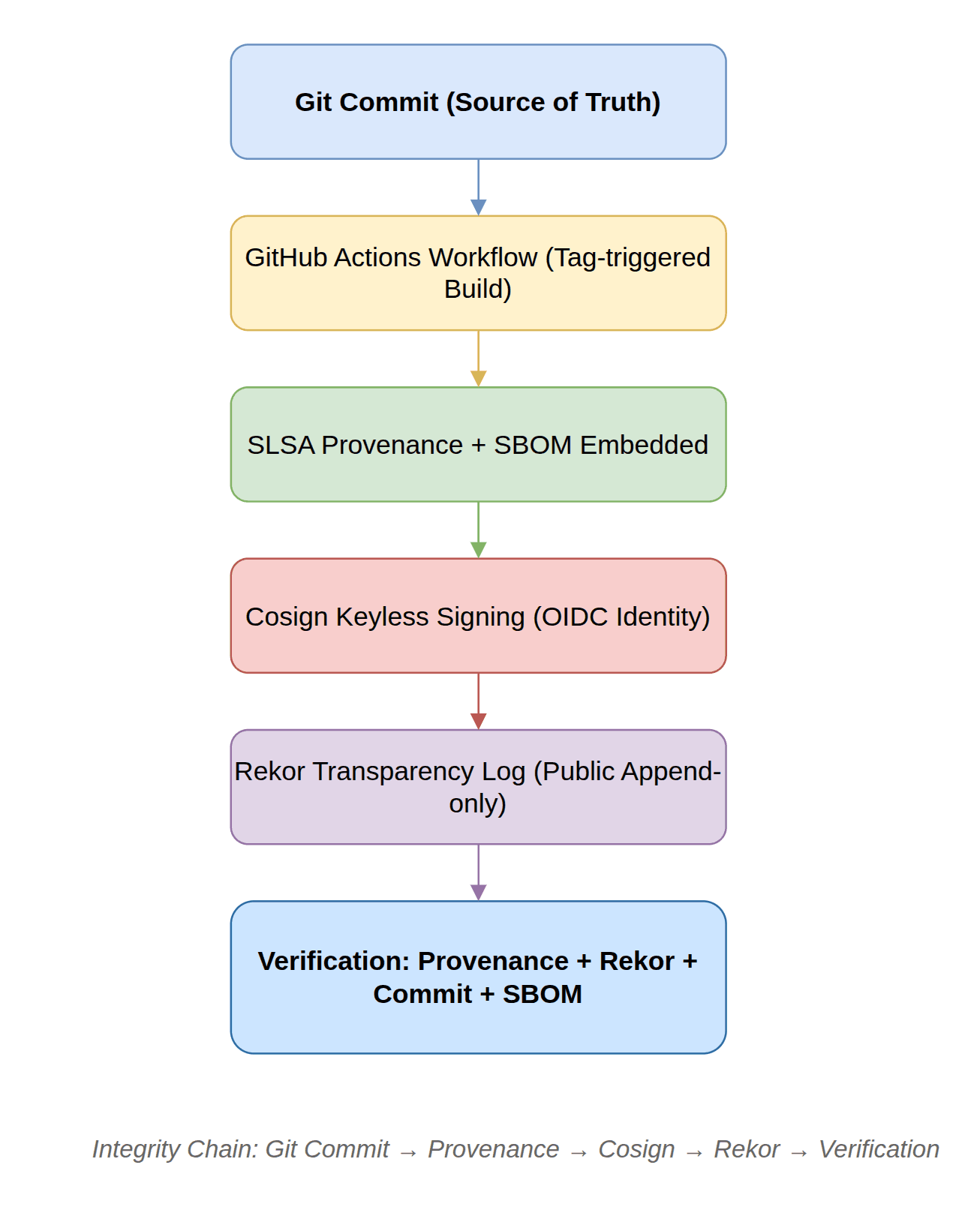
Secure CI/CD Pipeline: SLSA Level 3 provenance with keyless signing and transparency logs
SLSA Level 3 Provenance
Workflow: .github/workflows/docker-push.yml
Trigger: push: tags: ['v*.*.*']
Permissions: id-token: write
Each tagged build produces:
- SLSA provenance: Includes the source URI and commit SHA.
- SBOM (SPDX 2.3): Lists dependencies and package metadata.
- Immutable tags:
docker.io/fystack/apex/{service}:{version}and{version}-{sha}.
Verify Provenance
docker buildx imagetools inspect docker.io/fystack/apex/api:v1.0.0 \
--format '{{ json .Provenance.SLSA }}' | jq -r '.predicate.buildDefinition.resolvedDependencies[0].uri'
# Expected: https://github.com/fystack/apex/commit/<sha>
Cryptographic Signing (Cosign Keyless)
Each image and attestation is signed by GitHub Actions' OIDC identity, eliminating private key management risks. Signatures are stored in Rekor, a public, append-only transparency log.
Signature Generation (within CI):
Sign Image
cosign sign \
--identity-token "https://token.actions.githubusercontent.com" \
docker.io/fystack/apex/api@sha256:<digest>
Signature Verification:
Verify Signature
cosign verify \
--certificate-identity-regexp="github.com/fystack/apex/.github/workflows/docker-push.yml@*" \
--certificate-oidc-issuer="https://token.actions.githubusercontent.com" \
docker.io/fystack/apex/api:v1.0.0
This proves:
- The image was built by a trusted GitHub workflow.
- The signature is valid and timestamped in Rekor.
- No manual signing keys exist that could be stolen or misused.
3. Incident Verification & Recovery
If a hack, image tampering, or insider attack is suspected, follow this verification sequence to prove authenticity:
Step 1 — Retrieve Provenance
Retrieve Provenance
cosign verify-attestation --type slsaprovenance docker.io/fystack/apex/api:v1.0.0 | jq .
Reveals source commit URI, repository, and workflow identity.
Step 2 — Verify Signature and Transparency Record
Verify Signature & Rekor Log
cosign verify \
--certificate-identity-regexp="github.com/fystack/apex/.github/workflows/docker-push.yml@*" \
--certificate-oidc-issuer="https://token.actions.githubusercontent.com" \
docker.io/fystack/apex/api:v1.0.0
rekor-cli search --artifact docker.io/fystack/apex/api:v1.0.0
Confirms the image signature is valid and its record exists in Rekor's public log with a timestamp.
Step 3 — Verify Git Commit Integrity
Verify Commit
git show <commit-sha>
Confirms the commit referenced in provenance still exists and wasn't rewritten.
Step 4 — Cross-Check SBOM
Verify SBOM
docker buildx imagetools inspect docker.io/fystack/apex/api:v1.0.0 | jq '.SBOM'
Confirms dependencies match the verified source repository and SBOM metadata.
Final Proof Chain:
Proof Chain
Rekor Timestamp → Cosign Signature → Provenance Commit URI → Git Commit Hash
If all four align, the image is proven to originate from a trusted, untampered commit.
Verification Checklist
Step | Command | Expected Output |
|---|---|---|
| cosign verify ... | Success message showing GitHub OIDC identity |
| rekor-cli search --artifact <image> | Log entry with timestamp |
| cosign verify-attestation --type slsaprovenance ... | Commit URI and workflow ID |
| git show <sha> | Commit metadata matches provenance |
| docker buildx imagetools inspect ... | SPDX 2.3 metadata present |
4. Hardening & Best Practices
Control | Purpose |
|---|---|
Pin base images by digest | Prevents supply chain drift and tag rewriting. |
Immutable version tags | Disallow overwriting existing version tags. |
Require signed commits in GitHub | Ensures authenticated source commits. |
Registry content trust | Enforce OCI registry tag immutability. |
SBOM embedding | Ensures dependency traceability. |
Immutability policy enforcement | Prevent registry pushes to existing tags. |
Audit with immudb | Store verification results (image digest + commit SHA) in tamper-proof logs. |
5. Summary
This build pipeline gives Fystack a provable, cryptographically verifiable lineage from Git commit to deployed container.
It ensures:
- Transparent and auditable supply chain provenance.
- No secret key dependency.
- Resistance to insider or external tampering.
- Compliance alignment with SLSA Level 3 and Sigstore best practices.
In short: every Fystack container is not just reproducible — it's provably authentic.